Configuration D-Link Web Smart Switch User Manual
6
6
6
6
Forwarding Port Settings: Click to enable or disable the function.
Click Apply to implement the changes made.
Use the From Port drop-down menu to specify a port or all ports from the Switch, tick the ports under To
Port, and click Apply to implement the changes made and display the settings at the table below.
Click Select All button to check all ports. Click Clear to uncheck all ports.
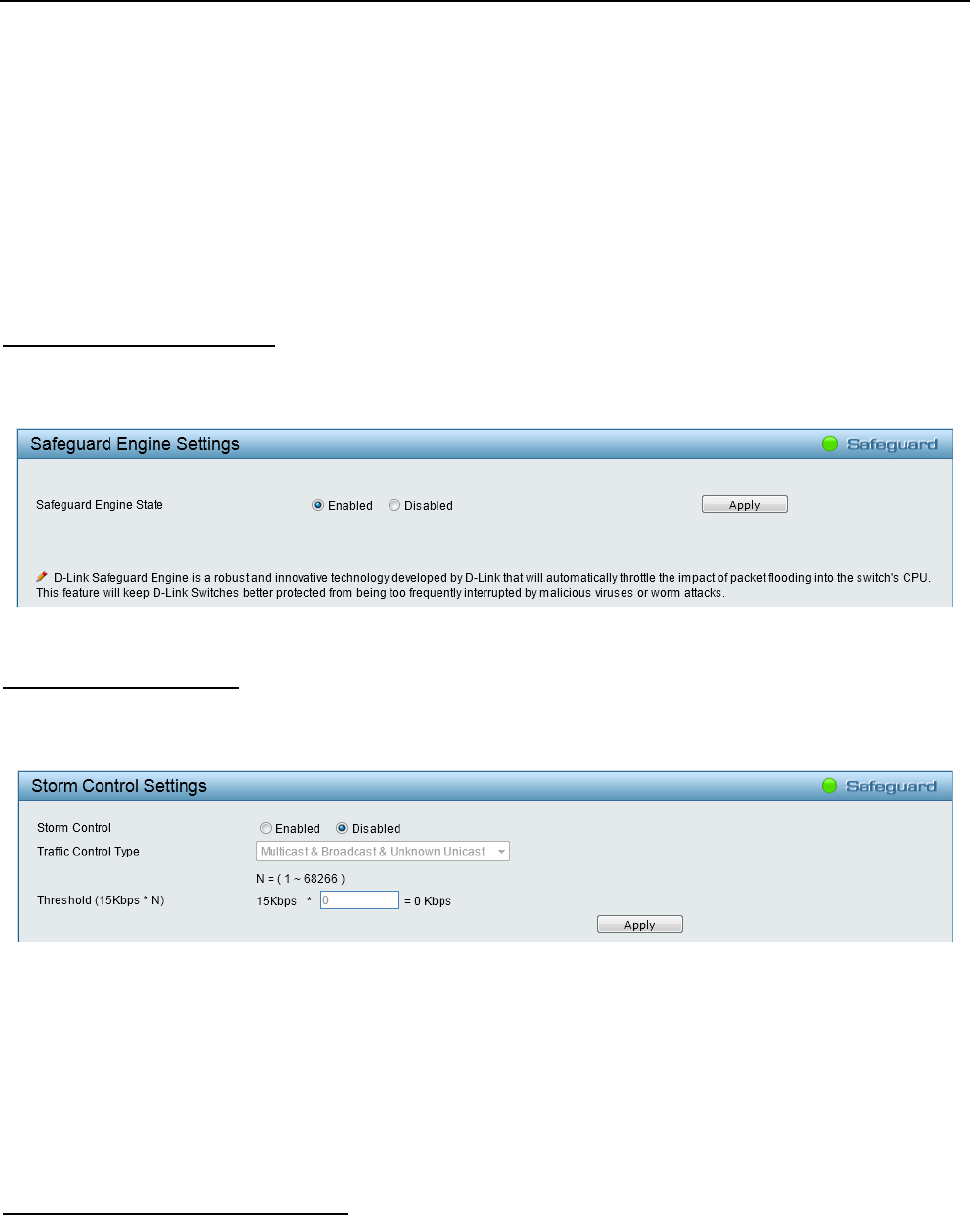
D-Link’s Safeguard Engine is a robust and innovative technology that automatically throttles the impact of
packet flooding into the switch's CPU. This function helps protect the Web-Smart Switch from being
interrupted by malicious viruses or worm attacks. This option is enabled by default.
Security > Safeguard Engine
Figure 4.76 – Security > Safeguard Engine
The Storm Control feature provides the ability to control the receive rate of broadcast, multicast, and
unknown unicast packets. Once a packet storm has been detected, the Switch will drop packets coming into
the Switch until the storm has subsided.
Security > Storm Control
Figure 4.77 – Security > Storm Control
Storm Control Type: User can select the different Storm type from Broadcast Only, Multicast & Broadcast,
and Multicast & Broadcast & Unknown Unicast.
Threshold (15Kbps * N): If storm control is enabled (default is disabled), the threshold is from of 15 to
1,024,000 Kbit per second, with steps (N) of 15Kbps. N can be from 1 to 68266.
Click Apply for the settings to take effect.
ARP spoofing, also known as ARP poisoning, is a method to attack an Ethernet network by allowing an
attacker to sniff data frames on a LAN, modifying the traffic, or stopping the traffic (known as a Denial of
Service – DoS attack). The main idea of ARP spoofing is to send fake or spoofed ARP messages to an
Ethernet network. It associates the attacker's or random MAC address with the IP address of another node
such as the default gateway. Any traffic meant for that IP address would be mistakenly re-directed to the
node specified by the attacker.
Security > ARP Spoofing Prevention
A common DoS attack today can be done by associating a nonexistent or specified MAC address to the IP
address of the network’s default gateway. The malicious attacker only needs to broadcast one gratuitous
ARP to the network claiming to be the gateway, so that the whole network operation is turned down as all
packets to the Internet will be directed to the wrong node.


















