Audacity
©2008 Audacity Audio Page 21 of 29
WiFi is a good option for in-office use. It is fast and quite efficient with
the right hardware. It will not work once the Author leaves the office.
On the WiFi tab, program the IP address of the PC running the LAM
application. You can find this in the LAM application under Manage,
Folder Settings, and Wireless Network Input. Look for the Local IP
Address. The files are sent to the LAM desktop application and LAM
processes them automatically just as if they were transferred via a
cable.
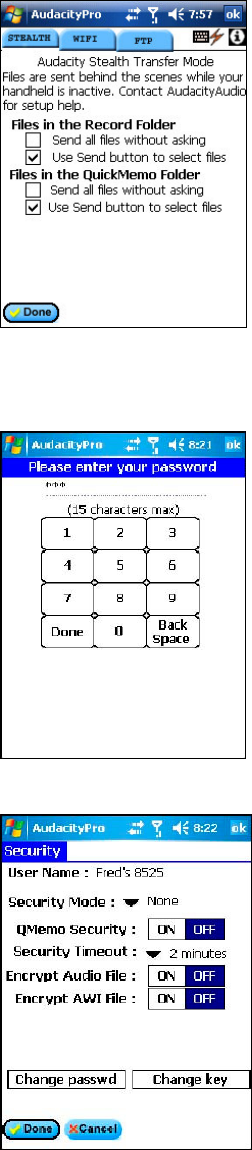
The third and best option is Audacity Stealth. It is designed to handle
large audio files from any location. It uses the cellular network and is
robust enough to handle cellular irregularities with ease. It is the
easiest to use and offers the most options for easy file delivery. It is
provided as part of the Audacity Communicator service. Audacity
Communicator is a comprehensive service offering including the
handheld recorder, file transport, file management, notification, and
transcription. It makes communicating with the office much more efficient for a mobile professional.
Audacity Audio would be happy to discuss how it could help you.
Security Setup
Tapping on Security Setup from the Options menu will display a
screen prompting you to enter the security code. The default entry
code is 123. Once you have entered the code you can set various
security levels, the security timeout period, and control encryption.
You also have a means to change the security password
(recommended), or change the encryption key. The default setting is
for no security.
Security Mode: - The choices are 'None', Playback Only', or
Full'. Full requires you to enter a security key each time you use
the program after the security timeout period. The security code
will not be needed again as long as you continue to Record or
Playback. The security timeout period begins once activity
ceases. The default timeout is 2 minutes. Consequently, the
code will not need to be entered until 2 minutes after activity ceases.
'Playback Only' does not require a key for recording. Playing
back a file just recorded (within the security timeout period) does
not require you to enter the security key, but does require a key
in order to play a file if the timeout period has expired. The
security key is required to Play or Append to any closed file.
QMemo Security – Specifies whether or not to enforce security
for QuickMemo files.
Security Timeout – Sets the amount of time an entered security
key remains valid. The choices are 15 or 30 seconds, 1, 2, 5, 10
or 30 minutes, and 1 hour.
Encrypt Audio File: Determines if the audio file will be stored in
an encrypted format.
Encrypt AWI Files – Determines if the associated AWI files will
be stored in an encrypted format.
If using encrypted files, you will need to set an encryption key. Any combination of letters, numbers,
and special characters may be used (up to 15 characters). Either the LAM or RAM, application will be
needed to decrypt the files. CAUTION! The encryption key must be set and must match on both ends
for the process to work.
