!
54
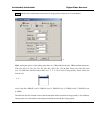
The picture below (6-28) is the other user sending request to the existing user with control.
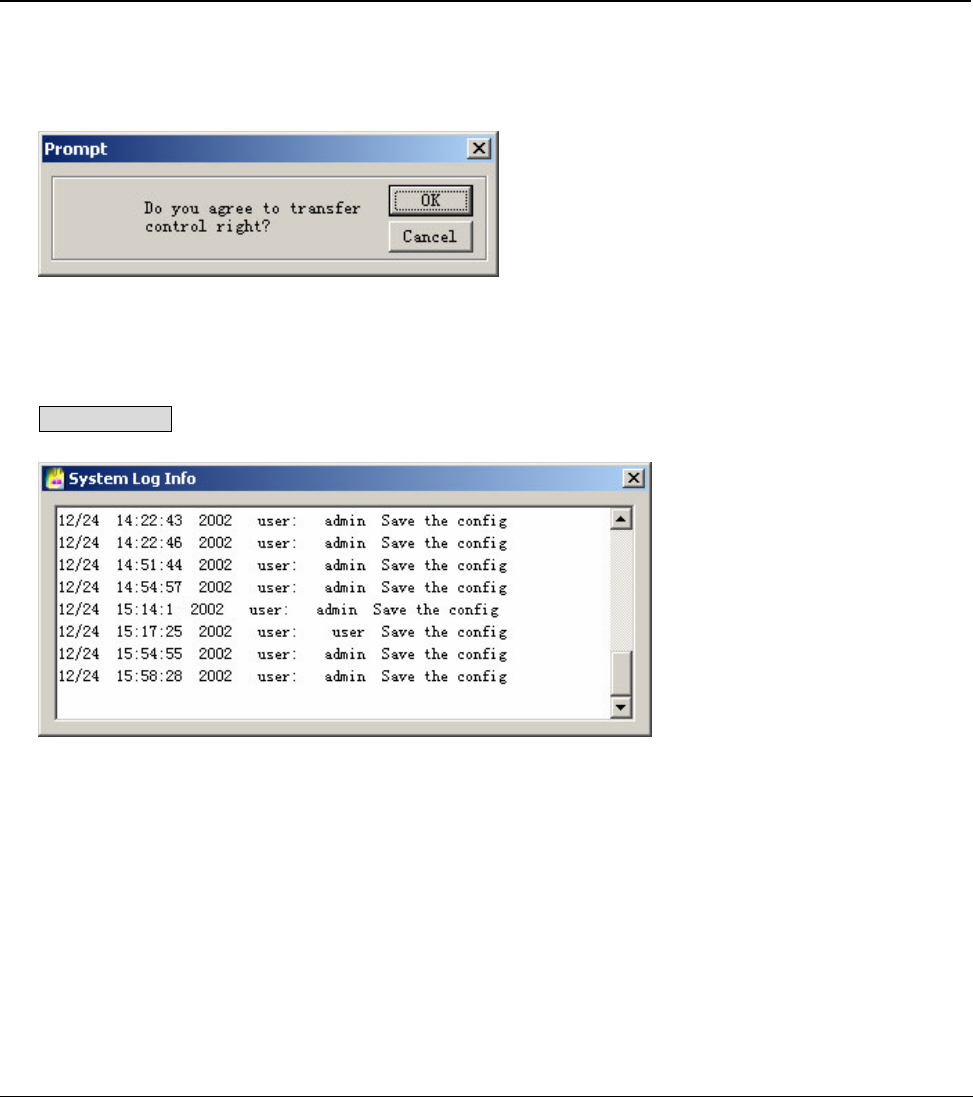
Log informationThe operations on the system are all recorded in log information.