MultiPrime
228 RSA BSAFE Crypto-C Developer’s Guide
You are encrypting 8 bytes, so you do not need to worry about that constraint.
However, the output of RSA encryption is the same size as the modulus, as described
in “The RSA Algorithm” on page 51. That means you must set the output buffer,
which will hold the encrypted data, to be the same size as the modulus. Your
modulus is 512 bits, or 64 bytes.
Note: The input to the RSA algorithm must also be the same size as the modulus,
but
AI_PKCS_RSAPublic will automatically pad.
The description of
AI_PKCS_RSAPublic notes that “B_EncryptUpdate and
B_EncryptFinal require a random algorithm.” The random number generator is for
the padding. You do not need random bytes, only an algorithm that can generate
them. Although RSA encryption is not as slow as key pair generation, you will not see
an immediate response. Use a surrender context so that you know the program is
running and has not frozen:
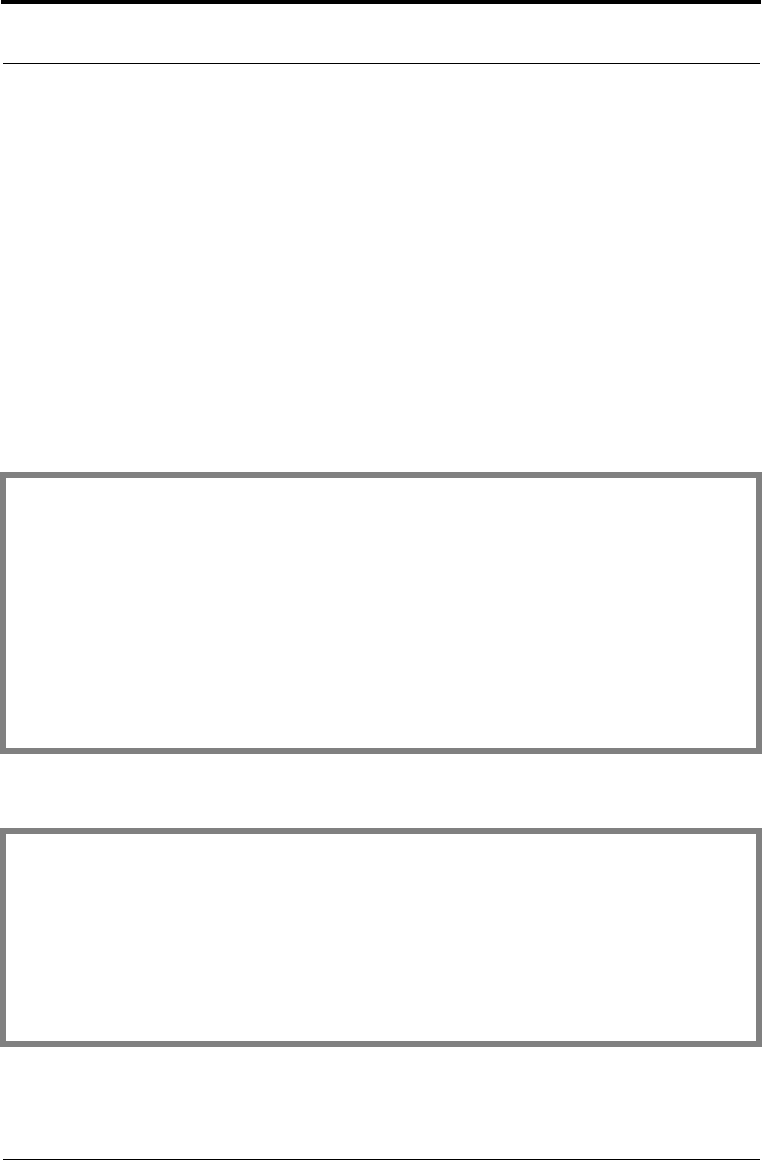
Step 5: Final
#define BLOCK_SIZE 64
unsigned char encryptedData[BLOCK_SIZE];
unsigned int outputLenUpdate;
/* generalFlag is for the surrender function.*/
generalFlag = 0;
if ((status = B_EncryptUpdate
(rsaEncryptor, encryptedData, &outputLenUpdate,
BLOCK_SIZE, (unsigned char *)dataToEncryptWithRSA, 8,
randomAlgorithm, (A_SURRENDER_CTX*)NULL_PTR)) != 0)
break;
unsigned int outputLenFinal;
/* generalFlag is for the surrender function.*/
generalFlag = 0;
if ((status = B_EncryptFinal
(rsaEncryptor, encryptedData + outputLenUpdate,
&outputLenFinal, BLOCK_SIZE - outputLenUpdate,
randomAlgorithm, (A_SURRENDER_CTX*)NULL_PTR)) != 0)
break;
