Decrypting the Introductory Example
28 RSA BSAFE Crypto-C Developer’s Guide
Step 5: Final
In the “Introductory Example” on page 9, the plaintext was a string. Therefore, we can
compute the sum of
decryptedLenUpdate
and
decryptedLenFinal
to determine how
many characters make up the decryption.
Note: For some algorithms, the decrypted data may not be a string — for example,
when the
NULL-terminating character was not encrypted. In these cases, if you
want to print the decrypted data, you will not be able to because the data is in
binary form, not ASCII. You could print the binary data using
RSA_PrintBuf(), or you can convert the decrypted data. Crypto-C offers
encoding and decoding functions to convert between binary and ASCII. See
“Converting Data Between Binary and ASCII” on page 172 for more
information.
Step 6: Destroy
Always destroy objects when you no longer need them:
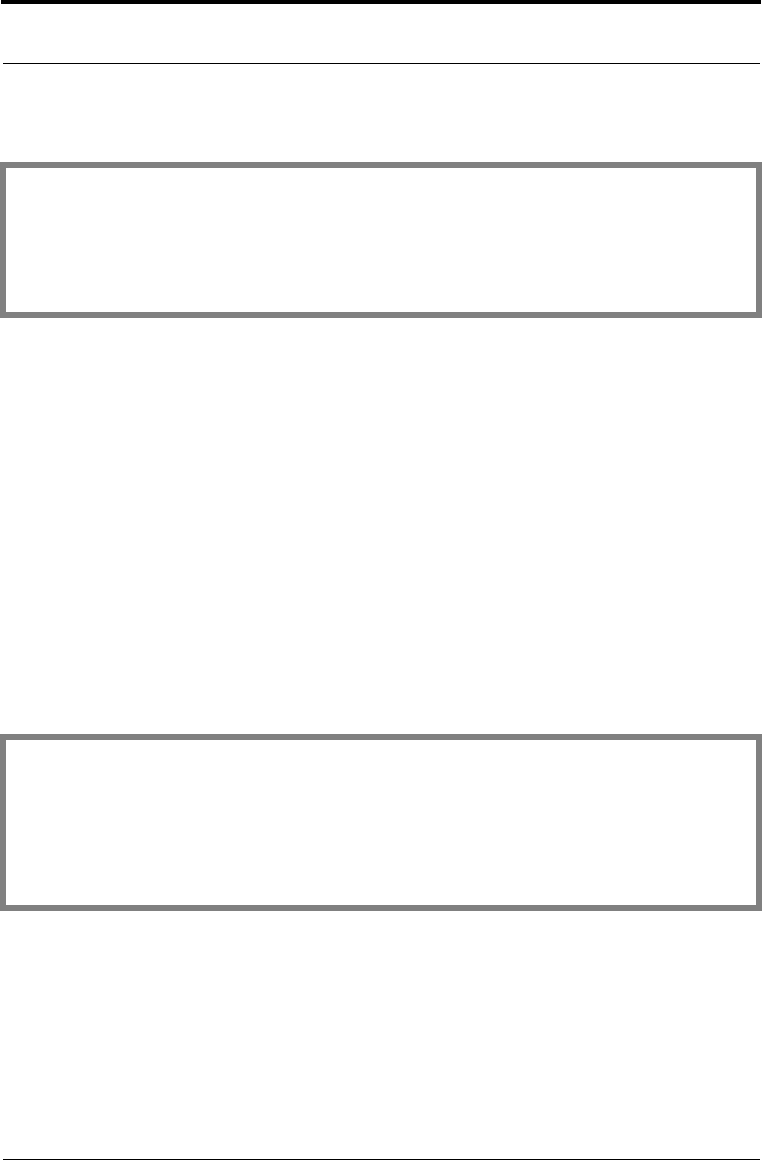
if ((status = B_DecryptFinal
(rc4Decrypter, decryptedData + decryptedLenUpdate,
&decryptedLenFinal, encryptedDataLen - decryptedLenUpdate,
(B_ALGORITHM_OBJ)NULL_PTR,
(A_SURRENDER_CTX *)NULL_PTR)) != 0)
break;
B_DestroyAlgorithmObject (&rc4Decrypter);
if (decryptedData != NULL_PTR) {
T_memset (decryptedData, 0, encryptedDataLen);
T_free (decryptedData);
decryptedData = NULL_PTR;
}
