18 C2641M (9/06)
DX8100 NETWORK PORTS
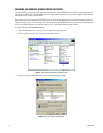
Table B describes the DX8100 default ports and their function. The DX8100 ports are classified either as user-changeable or fixed. You can
assign a user-changeable port a different number. In this case, a user-changeable port’s number must be assigned within the range of 5000 to
6535. If a port is assigned out of this range, the system displays a message alerting you that an invalid port number is being used. You cannot
assign a different number to a fixed port.
NOTE: Unless there is a conflict on your network, it is recommended that you do not change port numbers from their default settings. Make sure
any changes to port numbers are made consistently across all DX8100 servers and clients on a network.Client and server ports must be identical.
The DX8100 port functionality is summarized as follows:
• Base port: This port is configured at the DX8100 Network setup screen. The base port number is downloaded to the PC client system during
an IP scan. The port number can be modified at the DX8100 Site Setup screen.
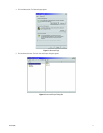
• Software Upgrade Port: This port is configured at the DX8100 Network setup screen. The upgrade port number is downloaded to the PC
client system during an IP scan. The port number can be modified at the DX8100 Site Setup screen. The PC client’s upgrade port number
must match the DX8100 server’s upgrade port number. For server-to-server software upgrades, both server software upgrade port numbers
must match.
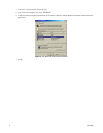
• Agent Port: This port is configured at the DX8100 Notification setup screen. You change the client emergency agent server listening port
using the Emergency Agent application running on the PC client system. For more information about changing the client emergency agent
listen port, see the Client Applications manual.
Table C lists other reserved port information.
FIREWALLS
Firewalls are used to keep external systems from exploiting vulnerabilities in the operating system that are linked to the Windows TCP/IP socket
system. Regardless of which port or service is under attack, the port must be open or at least visible in order for the malicious program to exploit
it. Firewalls render all ports that are not needed invisible and hence form an excellent protection against such attacks. Networked systems
exposed in anyway to the outside world (such as when connected to the Internet) should be equipped with a firewall.
Table B. DX8100 Network Ports
Port Number User-Changeable Function
9002 Yes DX8100 base port: Used for transmission of video, audio, and interface data
9003 Yes Software upgrade port: Used for remote upgrade of DX8100 software
9004 Yes Agent port: Used for emergency agent notification
9005 No Information port
13900 No Ping port
Table C. Other Reserved Port Assignments
Port Number Description
0 Not used
1–255 Reserved for well-known services at network communication
256–1023 Other reserved ports
1024–4999 Temporal client ports (OS allocates automatically)
5000–6535 User-defined ports