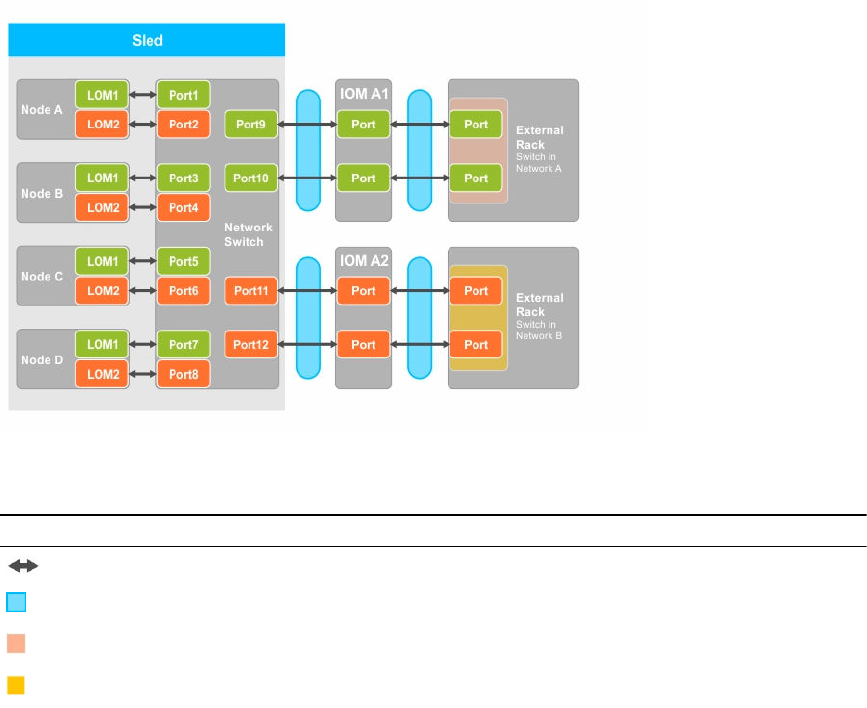
Figure 7. Isolated networks configuration
Table 7. Isolated networks configuration icon description
Icon Description
Network path
Trunk configuration or LAG
Local Area Network 1
Local Area Network 2
Enhanced network adapter isolation configuration
In this configuration, the individual node network adapters are isolated from other nodes in the sled, with
a dedicated IOM port mapped to LAN on motherboard (LOM) on each nodes. The LOM1 on each node is
operational, and it is recommended that the LOM2 must be disabled in the operating system. This
configuration functions when the TOR connections for each node within a sled are on the network layer
2 domain.
This configuration enhances security, as security features like firewalls are installed in the external rack
switches, and is useful in multi-tenant configurations.
30


















