Chapter 4 - RASFinder Software
RF300E/RF310E 47
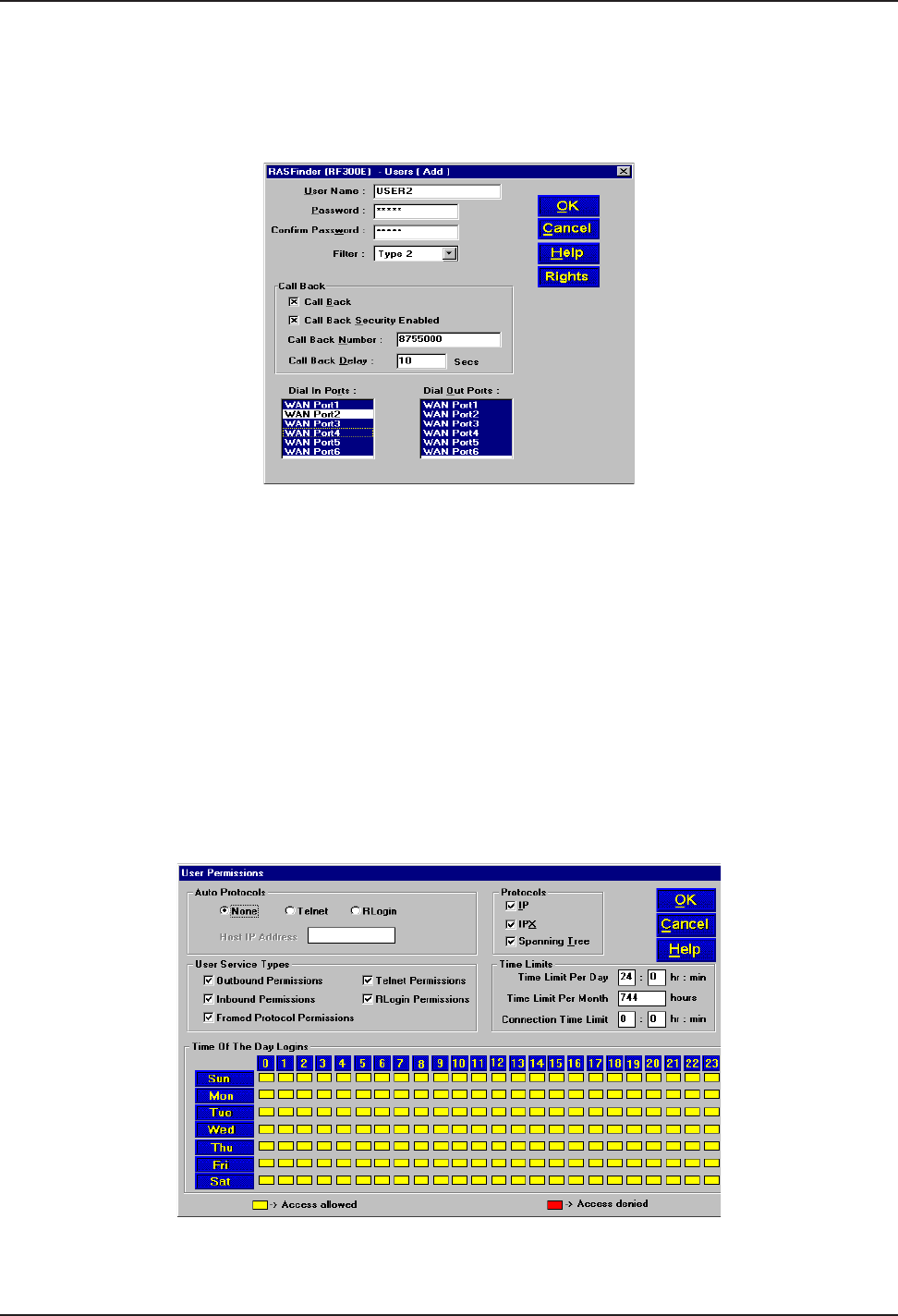
Before remote users can dial into the network, a user profile has to be set up in the proprietary
remote user database using the Remote User Data base utility. This data base utility is provided with
the RASFinder software. The RASFinder network administrator builds this database by adding
information (for one remote user at a time) via the Add Users dialog box. The user name and
password in this application must be negotiated between the RASFinder administrator and each
remote user.
User names can be up to 39 characters long, with any printable characters; however, no spaces are
allowed within the names. In our dialog box (above), we are using the User Name “User2.” The
letters will appear as all caps in the Users List; however, dial-in applications will treat the user names
as case-insensitive strings, enabling the users to enter their user names as all uppercase, all
lowercase, or a mixture of uppercase and lowercase.
A User Password of up to 7 characters should be given each user. In the Call Back group, the Call
Back option should be enabled (checked) for security purposes. If ONLY this option is checked, the
remote user would be asked to supply the callback numbers when they dial into the RASFinder. If
Call Back Security Enabled is also checked, the administrator controls the callback numbers through
the Call Back Number field. In our typical application, User 2’s phone number is 875-5000; therefore,
we enter this number in the Call Back Number field. In the Dial In Ports, we have assigned User2 to
WAN Port 2 with phone number 716-5466 assigned to it. This phone number will have to be entered
in the Phone Number field on remote User 2’s dial-up networking (My Connection) dialog box.
After the Add Users dialog box is filled in, you need to click the Rights button which brings up the
User Permissions dialog box.
The User Permissions dialog box enables you to assign protocol’s, user service type(s), time limits,
and time of day for each user to login. The Auto Protocols allow for no auto login, login via Telnet, or
