CHAPTER 3: OPERATION – USER FUNCTIONS 47
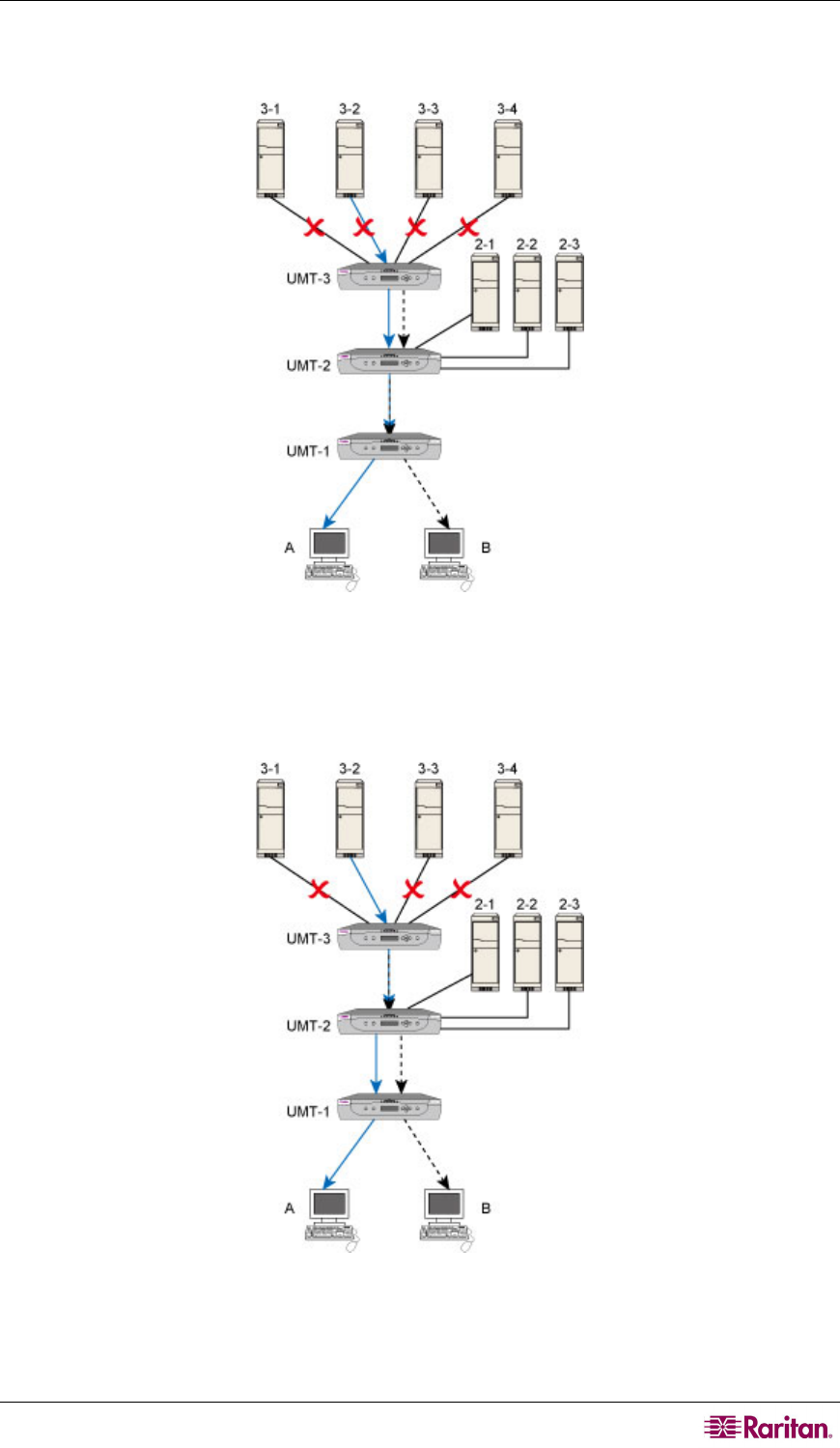
Instance 2: “B” user overlaps the path with “A” user’s in the segment between UMT-1 and UMT-2;
therefore, all servers connected to UMT-3 become inaccessible to the “B” user.
Figure 40 Path Overlapping Instance 2
Instance 3: “B” user overlaps the path with “A” user’s in the segment between UMT-2 and UMT-3;
therefore, only the server 3-2 connected to UMT-3 is accessible to the “B” user.
Figure 41 Path Overlapping Instance 3


















