System Administrator’s Guide
Document K14392V1 Rev A 185
07/07
Table 10–4 Security Happenstance
Situation Preventive and / or Last Resort Measures
vandalism - schedule onsite equipment inspections
- use access control to access Multi-Media units at sites
vandalism or
operator error
- schedule regular connections to each Multi-Media unit in your security
system
using many Multi
databases
- through training, discourage the use of many Multi dbs; using more than
one db, using different system passwords, is beyond the product’s design
and deemed unsafe.
- as a last resort, use the last valid password utility, as explained in
Last Valid
Password on p. 174.
breach of trust - refrain from communicating a system password to a Multi SA running
another Rapid Eye system
- ask security personnel to exercise vigilance if operators have accounts with
enough rights to jeopardize the data on a Multi-Media unit
- as a last resort, contact
Multi technical support for help, as explained in For
Questions on p.
22.
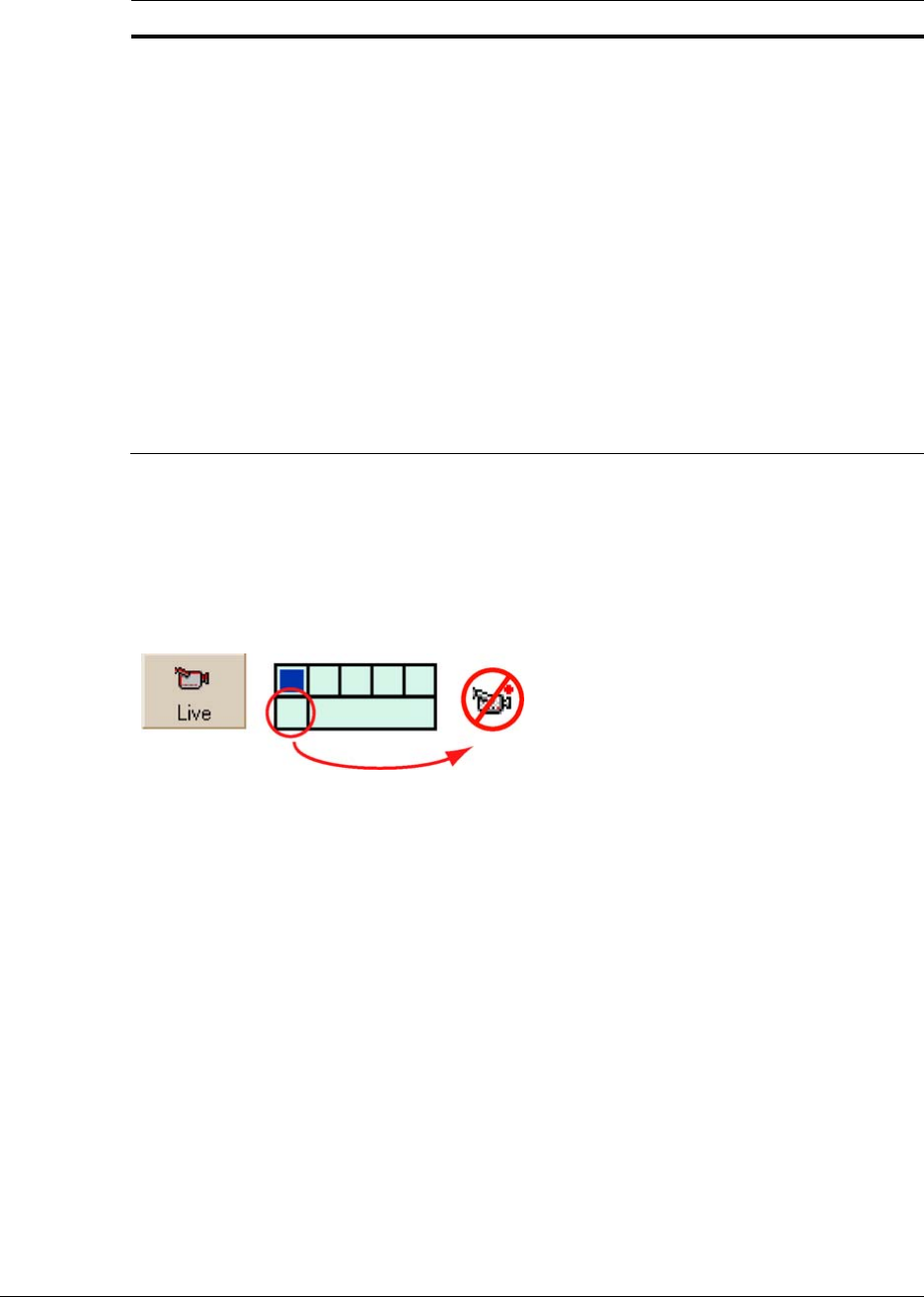
Compromising video recording
Setting the Recording of a camera to OFF. Video is not recorded when Recording is turned
OFF. This is easy to detect: each camera shows a recording meter during a Live Session. See
figure
10–11.
Fig. 10–11. Identifying a Camera that is Not Recording, in a Live Session.
If a corrupt operator turns Recording to OFF, Live would still work but no recording would be
available. Such abuse can be traced, as explained in
Tracing Events, below. See also Cameras,
on p.
65.
Camera brightness. Video may be compromised when the brightness setting on a camera is set
too high or too low. Your PTZ cameras may be installed in a way that they can be turned away
from the sun. See the Rapid Eye View Software Operator Guide.
Resetting the time/date. It can become complicated to analyze video “footage” after the time and
date of a Rapid Eye unit is changed recklessly. Recordings with incorrect time and date stamps
could be of no use to a court of law. You can trace events leading to such abuse, as explained
below, in Tracing Events. See also Unit’s Time Zone and Clock, on p. 56.
Scheduling cameras to not record. See
Scheduling: Configuration, p. 105. This feature is
designed to spare storage. It can be abused to defeat security. Use of the Boost button overrides
a turned OFF recording setting for video. See figure
10–12.
Countermeasures
.An effective countermeasure strategy includes
Camera Sabotage: Detection and scheduling short
Retrieval sessions on all cameras to spotcheck that Rapid Eye sites are recording as expected.
One can also check if the environment has diminished the effectiveness of a site. Verification can


















