18 SECURITY FUNCTIONS
113
18
18 SECURITY FUNCTIONS
These functions prevent theft, tampering, wrongful operation, illegal execution, etc. of a customer's assets saved on a
personal computer or in modules in the FX5 system as a result of illegal access by a third party. Use of the security functions
according to the following purposes.
Precautions
When a personal computer registered with a security key is misused by a third party, the outflow of program assets cannot be
prevented. For this reason, the customer must adopt sufficient measures as explained below:
• Personal computer antitheft measures (using a wire lock, etc.)
• Management of personal computer users (deletion of unwanted accounts, strict control of login information, introduction of
fingerprint authentication, etc.)
Also, when a personal computer registered with a security key malfunctions, locked project data cannot be accessed/viewed
or edited. Mitsubishi Electric Corporation cannot be held responsible for any loss that may occur as a result of this with the
customer, other individuals or organizations. For this reason, the customer must adopt sufficient measures as explained
below:
• Export registered security keys and import them into another personal computer.
• Store files containing exported security keys in a safe location.
Data protection
target
Purpose Function Reference
Projects To prevent illegal accessing and viewing of programs (in
program component units). (Password is used.)
Block password function GX Works3 Operating Manual
To prevent illegal accessing and viewing of programs (in
program file units). (Security key is used.)
Security key authentication
function
CPU Module To prevent illegal execution of programs. (Security key is
used.)
To prevent illegal reading/writing of files.
(Password is used.)
File password 32 function
To limit access from outside a specific communication
path. (Password is used.)
Remote password function GX Works3 Operating Manual
MELSEC iQ-F FX5 User's Manual
(Ethernet Communication)
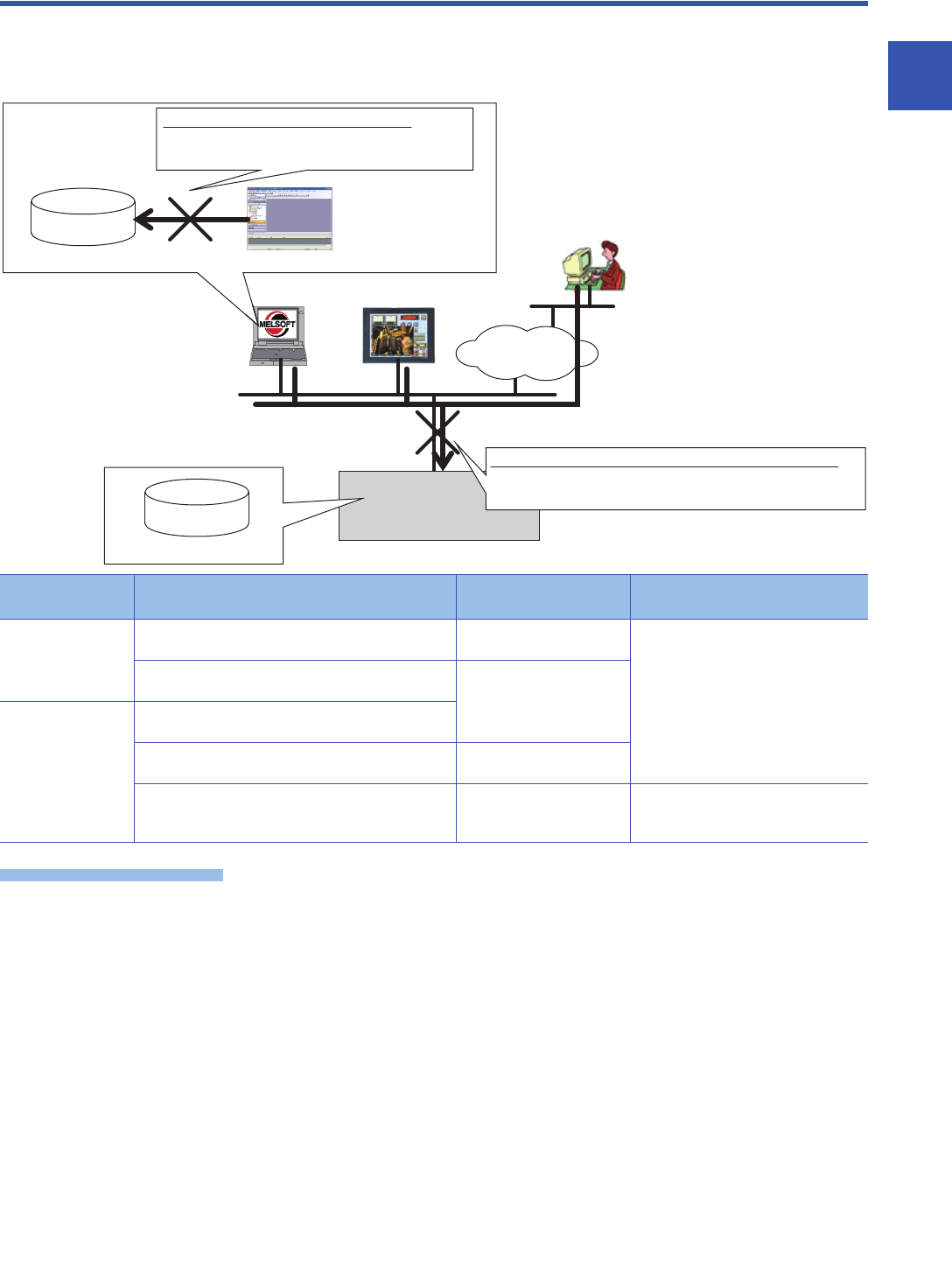
Customer assets
Customer assets
FX5 system
Engineering tool
GOT
(1) Protection of customer assets on PC
Prevents theft, tampering, or erroneous operation
through unauthorized access from third parties
(2) Protection of customer assets in FX5 system module
Prevents theft, tampering, or erroneous operation due to
unauthorized access by third parties
CPU module
Inter-
net/In-
Personal
computers
Personal computer
(outside the company)


















